Authentication
Authentication is an important part of any application. With a Django project that uses a decoupled frontend application such as μblog, authentication can be done in several different ways with different trade-offs.
Different ways to do authentication
Here are some ways that you can implement authentication:
- Use Django's built-in session authentication
- Use JSON Web Tokens (JWT) stored in localStorage
- Use JSON Web Tokens stored in memory/HttpOnly cookies
- Use Token Authentication from Django REST Framework
- Using third-party packages
Built-in session authentication
Using Django session authentication is what the Django REST Framework documentation recommends for user authentication. Some important points:
- You don't need to use any Django template views in order to use this method of authentication.
- This method of authentication requires no additional packages to be installed in our application
- Using session auth is secure and easy to implement
- Using session authentication is not stateless and each request must make a database query to check if the user is authenticated
- Logging users out is straightforward
- The
sessionidcookie is set as anHttpOnlycookie - The backend and frontend must use the same domain and subdomain
Using JSON Web Tokens (JWT) in localStorage
This method of authentication is very flexible and easy to implement and seems to be used very widely. However, there are some important concerns that need to be considered. Here are the import points regarding JSON Web Token authentication:
- Storing authentication data is
localStorageis not a best practice - You can easily authenticate requests where the backend and frontend are on different hosts. Some examples of
backend/frontendconfigurations that you can use with JWT authentication include:api.mydomain.com/app.mydomain.comlocalhost:8000/localhost:8080
- Using JWT authentication typically involves using a third-party package such as
djangorestframework-simplejwtopen in new window - If malicious JavaScript can run on the client, then an attacker could steal the JWT
accesstoken and start making authenticated requests. - If someone steals the tokens from your device (for example if someone copied the
accessandrefreshfrom the browser'slocalStoragewhen you are not at your device), then an attacker could use the stolen tokens to make authenticated requests, even if you log out. Logging only deletes theaccessandrefreshtokens from your browser'slocalStorage.
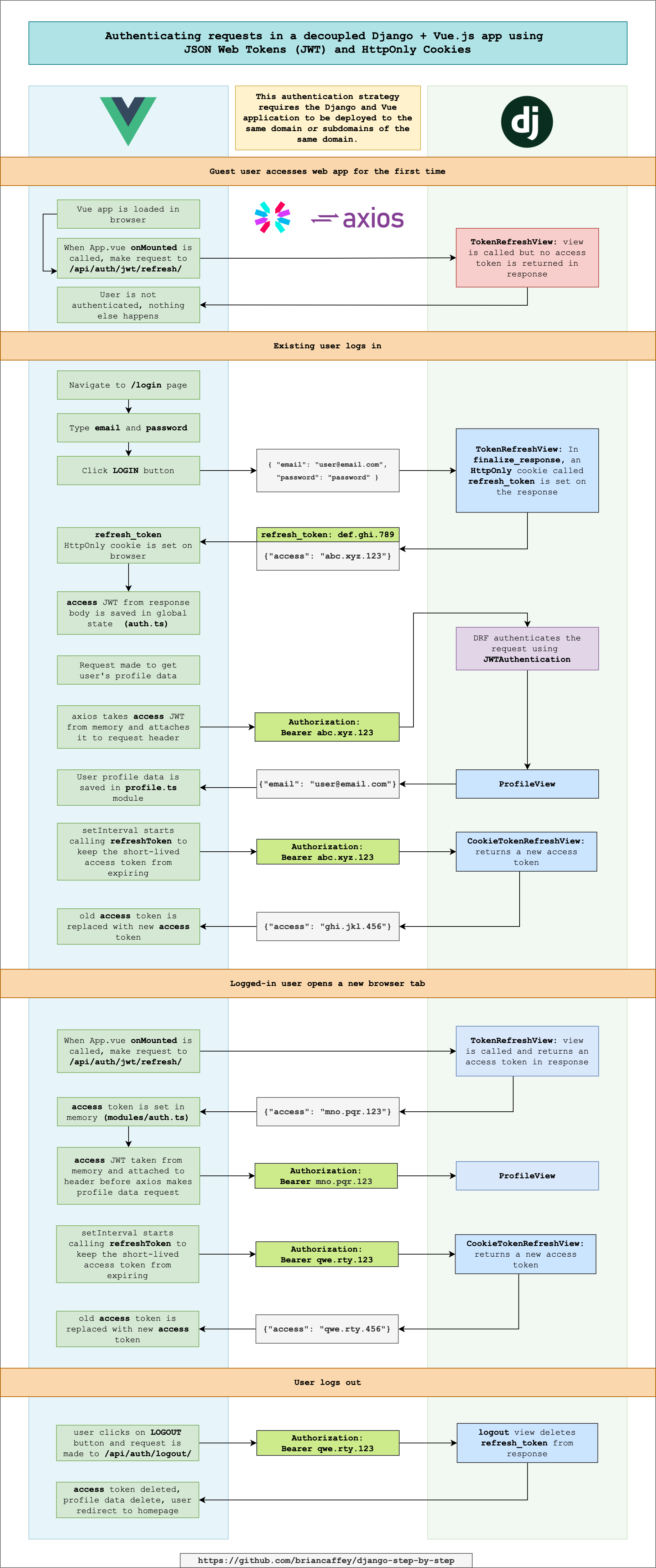
Use JSON Web Tokens stored in memory/HttpOnly cookies
This methods of authentication combines some of the features of JWT and session authentication.
- It takes some ideas and code from this GitHub issueopen in new window
- It generally follows the advice from this articleopen in new window
- It stores the
accesstoken in memory on the client - It sets the
refreshtoken in an HttpOnly cookie on the client - Logout can be done by deleting the
refreshtoken
Token Authentication from Django REST Framework
Token Authentication from the Django REST Framework is pretty straightforward. You can allow users to request an API token that they can use to authenticate requests. See https://www.django-rest-framework.org/api-guide/authentication/#tokenauthenticationopen in new window for more information.
Diagram of JWT authentication with HttpOnly cookies
Here is an overview of what the JWT authentication process looks like when using HttpOnly cookies: